Cybersecurity in Advanced Communication Systems: AI for Securing Cognitive IoT Networks
The Cognitive Internet of Things (CIoT) represents a significant advancement over traditional IoT by integrating cognitive computing capabilities into connected devices. In CIoT-based communication systems, devices not only collect and transmit data but also analyze it, learn from patterns, and make autonomous decisions. This cognitive ability enables more efficient spectrum usage, intelligent resource allocation, and adaptive communication in applications such as smart cities, healthcare, industrial automation, and agriculture. However, while CIoT greatly enhances the performance of modern communication systems, it also introduces serious security challenges. The increasing number of connected devices, along with their limited processing and storage capabilities, creates an environment highly vulnerable to cyberattacks.
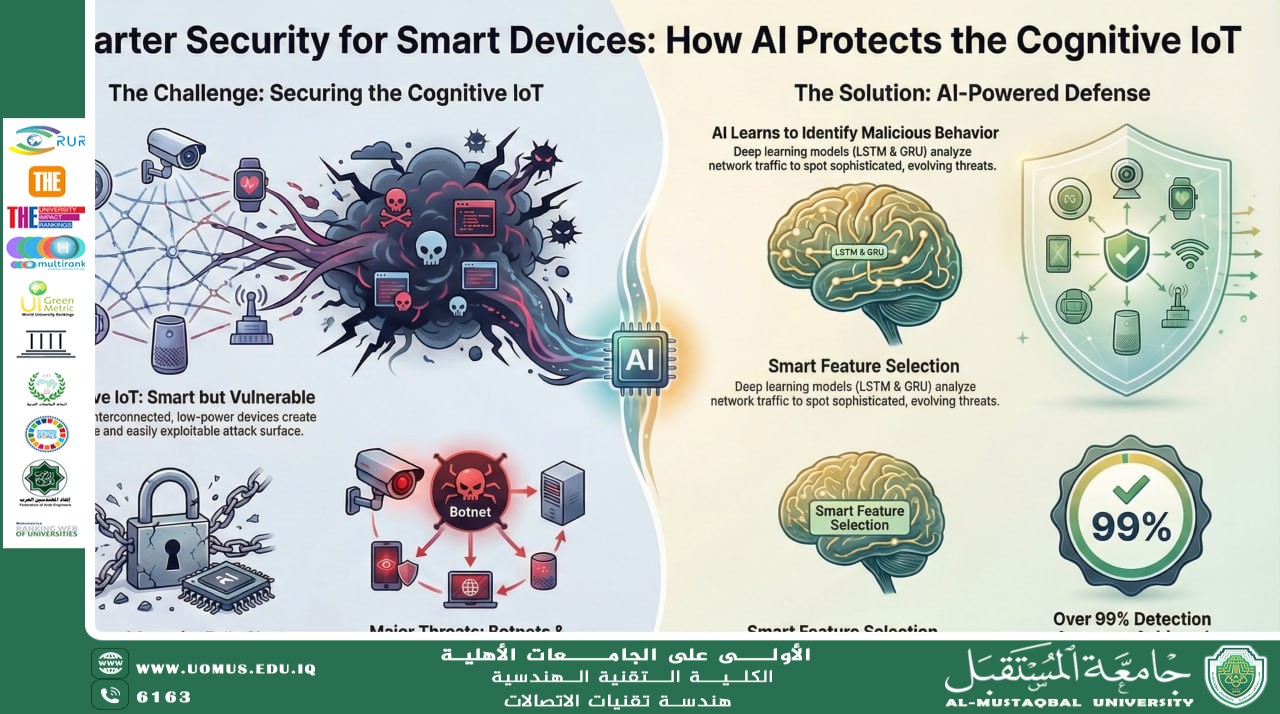
CIoT networks operate in dynamic and often hostile environments, where attackers can exploit weaknesses in communication protocols and device configurations. Malware families such as Mirai and Bashlite have demonstrated how IoT devices can be compromised and turned into botnets generating large volumes of malicious traffic. These attacks threaten not only individual devices but the entire communication infrastructure, as compromised nodes can be used to launch denial-of-service attacks, scan networks, or distribute further malware. Furthermore, since CIoT devices compete for limited wireless spectrum and often rely on cognitive radio technologies, attackers can also exploit spectrum sensing and data reporting mechanisms to disrupt network operations.
Traditional security approaches, which rely on fixed rules, predefined signatures, or complex cryptographic protocols, are not well suited for CIoT environments. Many devices lack the processing power to run sophisticated security software, and static defense mechanisms cannot adapt to evolving attack strategies. These limitations have led to growing interest in Artificial Intelligence (AI) as a foundation for securing advanced communication systems.
AI, particularly deep learning, provides powerful tools for analyzing complex, high-dimensional network traffic data. In CIoT networks, communication traffic is highly sequential and variable, making it suitable for recurrent neural network models such as Long Short-Term Memory (LSTM) and Gated Recurrent Units (GRU). These models are designed to capture temporal patterns and long-term dependencies in data, which are essential for detecting sophisticated cyberattacks that unfold over time. By learning how normal and malicious traffic behaves, deep learning systems can automatically classify network activity and identify threats with high precision.
An important aspect of applying AI to CIoT security is feature selection. Network traffic datasets may contain over a hundred attributes describing packet timing, entropy, jitter, and other statistical properties. Processing all these features would be computationally expensive and impractical for real-time deployment in IoT environments. Feature selection techniques, such as those based on random forests, are used to identify the most informative features that contribute most to accurate classification. By reducing the number of features to a small but highly relevant subset, the computational cost of the security system is significantly reduced while maintaining strong detection performance.
Experimental evaluations using real-world IoT traffic datasets infected with Mirai and Gafgyt botnets have demonstrated the effectiveness of this AI-based approach. These datasets contain millions of instances representing both benign and malicious traffic generated by commercial IoT devices. Deep learning models trained on selected features can classify different types of attacks, such as scanning, flooding, and command-and-control communication, with very high accuracy. In many cases, detection rates exceed 99%, indicating that AI-driven security frameworks can reliably distinguish between normal and malicious communication patterns.
Comparative analyses also show that deep learning models outperform traditional machine learning techniques such as logistic regression, support vector machines, and simple neural networks. While conventional models struggle to capture the complex temporal behavior of network traffic, LSTM- and GRU-based architectures are more effective at learning long-term dependencies and subtle variations in communication patterns. This makes them particularly suitable for CIoT environments, where attacks may develop gradually and exhibit complex signatures.
Despite these advantages, challenges remain. Reliance on predefined features means that some emerging threats may not be fully captured, and even optimized deep learning models can be demanding for extremely resource-constrained devices. To address these issues, future communication systems are expected to integrate edge and fog computing, allowing security analysis to be performed closer to IoT devices without overwhelming them. Additionally, privacy-preserving techniques such as federated learning and differential privacy are being considered to ensure sensitive data remains protected during model training and operation.
In conclusion, securing Cognitive IoT networks is critical for the reliability of advanced communication systems. AI, supported by deep learning and intelligent feature selection, offers an effective and scalable solution to this challenge. By enabling accurate, adaptive, and resource-efficient detection of cyberattacks, AI-based security frameworks play a central role in protecting the future of intelligent communication infrastructures.
Future University First in Iraq