Data Encryption and Transmission Through Channels
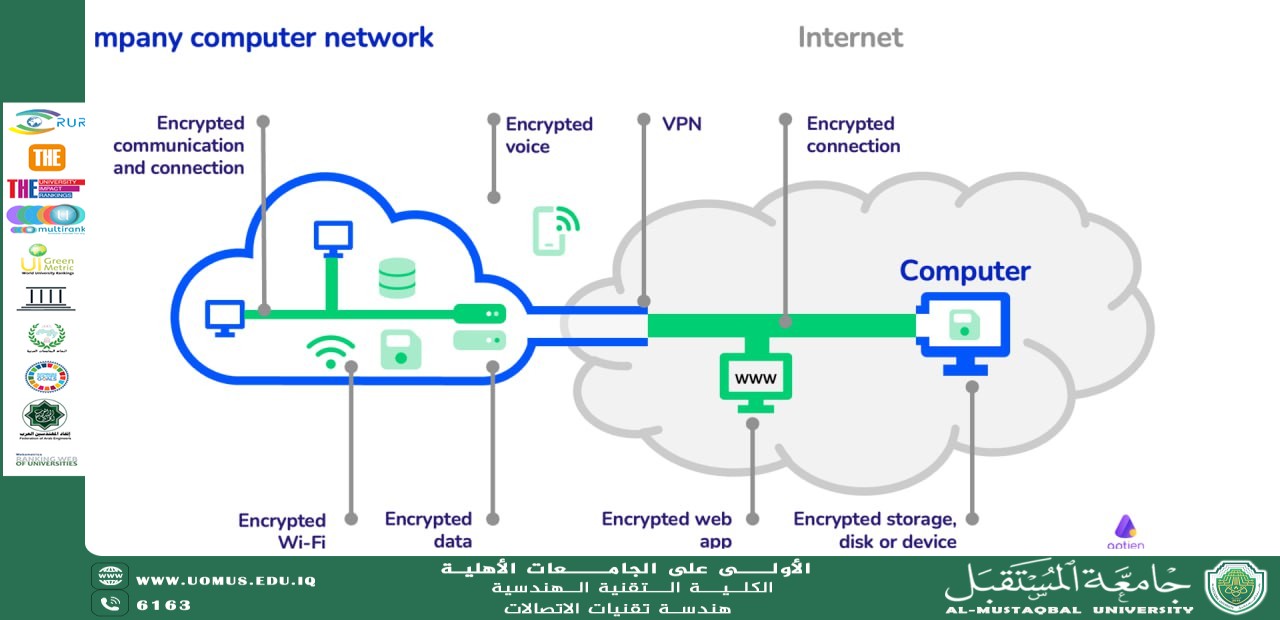
In the digital age, data is an invaluable currency. However, the internet infrastructure—such as optical fiber and Wi-Fi networks—was originally designed for connectivity rather than security. These channels are like public highways; without protection, sensitive information transmitted through them becomes vulnerable to interception. Data encryption acts as a crucial shield that ensures information remains secure during transmission.
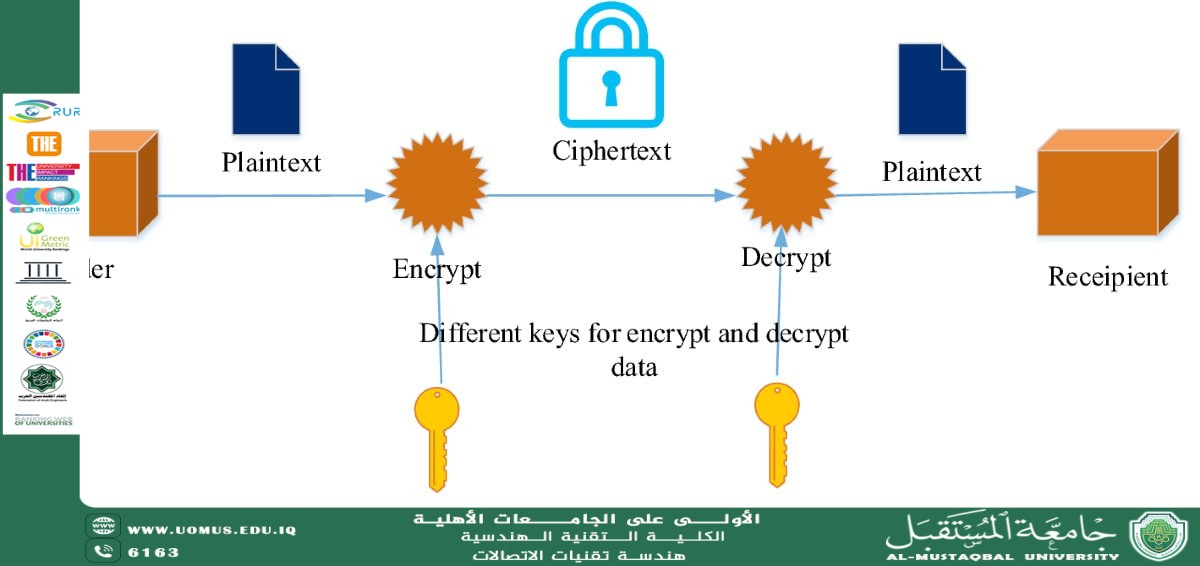
Encryption is the process of transforming readable “plaintext” into unreadable “ciphertext” using complex algorithms and cryptographic “keys.” Its primary goals are confidentiality (authorized access only), integrity (protection against tampering or modification), and authentication (verifying identities).
There are two main types of encryption: Symmetric encryption, which relies on a single secret key used for both encryption and decryption. It is fast and efficient for large data volumes but suffers from the challenge of securely distributing the key before communication begins. Asymmetric encryption overcomes this issue by using a pair of keys: a public key used for encryption and shared openly, and a private key used for decryption and kept strictly secret. Although it is slower, asymmetric encryption is essential for initial authentication and secure key exchange.
Transmission channels are inherently untrusted environments prone to eavesdropping and manipulation. Therefore, data must be secured before entering the channel. In practice, secure protocols like SSL/TLS (used in HTTPS connections) combine both encryption types to achieve efficiency and security together. During the initial handshake process, asymmetric encryption verifies the server’s identity and enables the secure exchange of a secret. This secret is then used to generate a temporary symmetric “session key,” which encrypts the actual data flowing through the unsecured channel with high speed.
Ultimately, while physical channels remain vulnerable, modern encryption ensures that even if data is intercepted mid-transit, it remains useless to unauthorized parties—providing the foundation of digital trust.
Future University The First in Iraq